This tutorial shows how to install a certificate using the traditional approach of using a Certificate Signing Request (CSR) with an online CA service. We recommend that you instead use the free let's encrypt service.
See Also: Automatic SSL certificate installation with Let's Encrypt.
Installing an SSL certificate is not required unless you need secure communication for your web applications running on the server.
We need to use a well known Certificate Authority (CA) to sign our certificate in order to get browsers to accept a secure connection without popping up a warning. Well known CAs have their public certificate pre-installed in all major operating systems (Windows/Linux/Mac). If you are not using a well known CA, you will have to manually install the CAs certificate in all operating systems (or browsers) that you plan on using.
We recommend reading the tutorial Certificate Management for Embedded Systems if you are new to certificate management. The tutorial provides a good introduction to SSL certificate management and the chain of trust that leads up to the CA (root) certificate.
We must perform the following steps for creating and installing a certificate.
Creating a private key and a Certificate Signing Request (CSR) can be done by using the OpenSSL command line tool. As an alternative (or if you find the OpenSSL command line tool difficult to use), download and install our Certificate Management Tool. This tool is designed for users that want to act as their own CA, but the tool can also be used for creating a private key and a CSR that can be signed by a well known CA.
If you use our Certificate Management Tool, make sure you create an RSA root certificate. Well known CAs that can sign ECC certificates are currently not common. After creating the RSA root certificate (CA certificate), proceed to creating a certificate for your own domain name. Make sure to carefully follow the instructions in the Certificate Management Tool. When you have created the certificate, the files of interest will be:
The domain simplemq.tk is what we used when we signed our certificate. Look for files with the name including your domain name. Note: the Certificate Management Tool also created a public certificate signed with the CA initially created by the Certificate Management Tool, but we will not use this certificate. Instead, we will have a well known CA sign our CSR (csr-simplemq.tk.req).
Make sure you save the private key and the CSR in a safe (and trusted) place. You can use the CSR whenever you need to create/sign a new certificate.
The following instructions shows how to obtain a free 90 day certificate from Comodo. You need to repeat the process (except for creating a private key and CSR) after 90 days. Signing and installing certificates are a bit tedious; thus you may consider using a paid for CA service that provides a certificate valid for three years.
Navigate to Comodo's free SSL certificate page and click the free certificate button. Open the CSR you created in the step above in an editor, select all, and copy the data. Paste this data into the CSR field at the Comodo's web site. Select "OTHER" for server software and click Next. Follow the wizard.
You will eventually get to a page where you have to validate that you own the domain name.
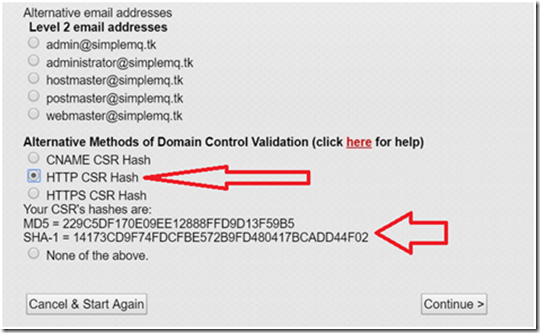
Figure 4: Select HTTP CSR Hash as validation method
Since you do not have an email account setup with the domain name, select HTTP CSR Hash as validation method. Assuming you have your online www directory mapped to your local computer, go ahead and create a file with the name <MD5 hash of CSR>.txt on the mapped drive. Copy the SHA-1 hash from Comodos web site and paste into this file. The file should have two lines:
Before clicking continue in the Comodo wizard, make sure you can open the file you just created by navigating to:
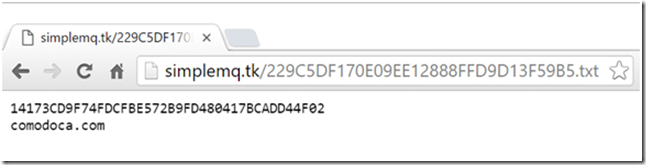
Figure 5: Screenshot of our domain validation file
Click continue in the Comodo wizard and complete your registration.
You should receive an email from Comodo with the certificate after some time if you successfully completed the Comodo SSL wizard.
Unpack the content of the ZIP file (attached to the Comodo email) in an empty directory. The ZIP file should contain the following:
The ZIP file contains your certificate, two intermediate Certificate Authorities (CAs), and the Comodo's public root certificate (AddTrustExternalCARoot.crt). We will not use the public root certificate since this certificate is already known by your browser. The browser keeps well known CAs in a CA database. However, we need the two intermediate CAs since we need the chain of trust leading up to the Comodo's root certificate. See the Wikipedia article Chain of trust, section Computer security, for more information on how this works.
Using your favorite text editor, create a new file and call it yourdomain.cert. Open the above list of certificate and intermediate CAs in an editor one at a time. Copy the content of these files in the order listed into your new file. Do not add AddTrustExternalCARoot.crt. Save the file. The new file must contain: *yourdomainname*.crt, COMODORSADomainValidationSecureServerCA.crt, and COMODORSAAddTrustCA.crt.
The next step is to copy your private key and your assembled certificate to your online server.
The files we created for our server are:
| simplemq.tk.key | The private key created by the Certificate Management Tool |
| simplemq.tk.cert | Created by assembling certificate and intermediate CAs |
An easy way to transfer the files to your online server is to copy them using the WebDAV connection that is setup to the 'www' directory on your server. However, the files need to be placed in the parent directory and not in www -- i.e. the files must be placed in /home/mako. A simple solution to this problem is to create a soft link from 'www' to the parent directory. The following Linux command does this:
Notice that we create a link (.ROOT) that starts with a dot. Files and directories that start with a dot cannot be navigated into when accessing the server using a standard HTTP client; however, the authenticated WebDAV client can access this directory.
The following screenshot shows the complete set of commands we used for creating the soft link:
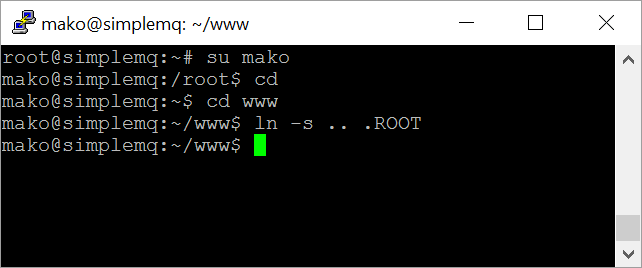
Figure 6: Creating a link from 'www' to the parent directory when logged in as the Linux user 'mako'
You can now simply drag and drop the files onto the mapped online server. The following screenshot shows how we copy the files to the .ROOT directory (the soft link pointing to the parent directory).
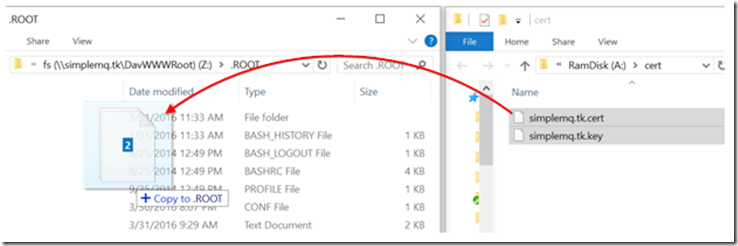
Figure 7: Copying the private key and certificate from PC to /home/mako
The names of the private key and the certificate must be added to the mako.conf file. The following example shows how we can directly open this file using Notepad from a PC. We have mapped the online 'www' directory as Z:.
Add the two following lines to mako.conf. Note, you must change the name of the key and the certificate to your own names.
Save the file and verify that the Mako Server can load your new key and certificate. The best way to do this is to run the Mako Server in the foreground since the server prints out error messages, if any to the console. The following screenshot shows how we stop the server running in the background, navigate to /home/mako, and start the server in the foreground as user (-u) 'mako'. As you can see from the screenshot below, the server successfully loaded our new key and certificate.
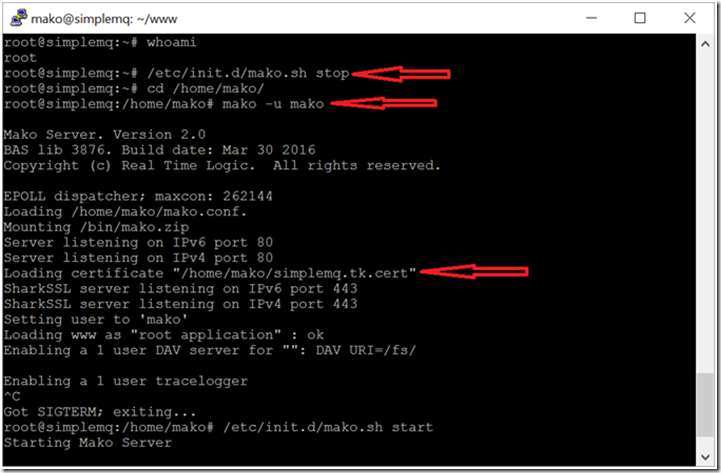
Figure 8: Verifying that Mako Server can load the certificate by running the server in the foreground
Stop the server running in the foreground by the using the command CTRL-C. You can then start the server in the background by using the command: /etc/init.d/mako.sh start
Navigate to https://your-domain-name. You should not get any certificate warning messages in your browser.
As a final test, you may navigate to https://www.ssllabs.com/ssltest/. Enter your domain name (hostname) and click submit. After some time, you should get a full report and no conflicts with your chain of trust.
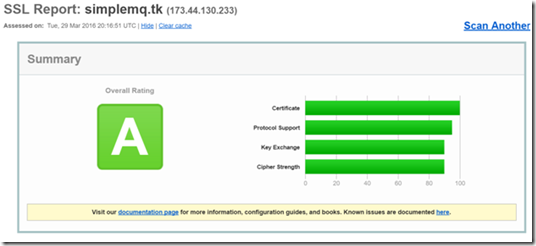
Figure 8: Verifying that Mako Server can load the certificate by running the server in the foreground
You may now setup a trusted and secure communication between any browser and the server by entering https://your-domain-name in the browser.
Our seasoned experts are ready to tackle your most pressing networking, security, and device management challenges. And if you're fueled by the DIY spirit, our rich collection of tutorials awaits to guide you. With us, you get the best of both worlds. Your project, our dedication.
Expedite your IoT and edge computing development with the "Barracuda App Server Network Library", a compact client/server multi-protocol stack and toolkit with an efficient integrated scripting engine. Includes Industrial Protocols, MQTT client, SMQ broker, WebSocket client & server, REST, AJAX, XML, and more. The Barracuda App Server is a programmable, secure, and intelligent IoT toolkit that fits a wide range of hardware options.
SharkSSL is the smallest, fastest, and best performing embedded TLS stack with optimized ciphers made by Real Time Logic. SharkSSL includes many secure IoT protocols.
SMQ lets developers quickly and inexpensively deliver world-class management functionality for their products. SMQ is an enterprise ready IoT protocol that enables easier control and management of products on a massive scale.
SharkMQTT is a super small secure MQTT client with integrated TLS stack. SharkMQTT easily fits in tiny microcontrollers.
An easy to use OPC UA stack that enables bridging of OPC-UA enabled industrial products with cloud services, IT, and HTML5 user interfaces.
Use our user programmable Edge-Controller as a tool to accelerate development of the next generation industrial edge products and to facilitate rapid IoT and IIoT development.
Learn how to use the Barracuda App Server as your On-Premises IoT Foundation.
The compact Web Server C library is included in the Barracuda App Server protocol suite but can also be used standalone.
The tiny Minnow Server enables modern web server user interfaces to be used as the graphical front end for tiny microcontrollers. Make sure to check out the reference design and the Minnow Server design guide.
Why use FTP when you can use your device as a secure network drive.
PikeHTTP is a compact and secure HTTP client C library that greatly simplifies the design of HTTP/REST style apps in C or C++.
The embedded WebSocket C library lets developers design tiny and secure IoT applications based on the WebSocket protocol.
Send alarms and other notifications from any microcontroller powered product.
The RayCrypto engine is an extremely small and fast embedded crypto library designed specifically for embedded resource-constrained devices.
Real Time Logic's SharkTrust™ service is an automatic Public Key Infrastructure (PKI) solution for products containing an Embedded Web Server.
The Modbus client enables bridging of Modbus enabled industrial products with modern IoT devices and HTML5 powered HMIs.